Investigators have primarily concluded that six people, divided into two groups, carried out Saturday’s attacks on publishers and bloggers.
This was done by tracking the IP addresses of the Twitter, Facebook and Google accounts that claimed responsibility for the attacks.
Seeking anonymity, an information technology (IT) expert who is assisting the investigation team, revealed this information to the Dhaka Tribune yesterday.
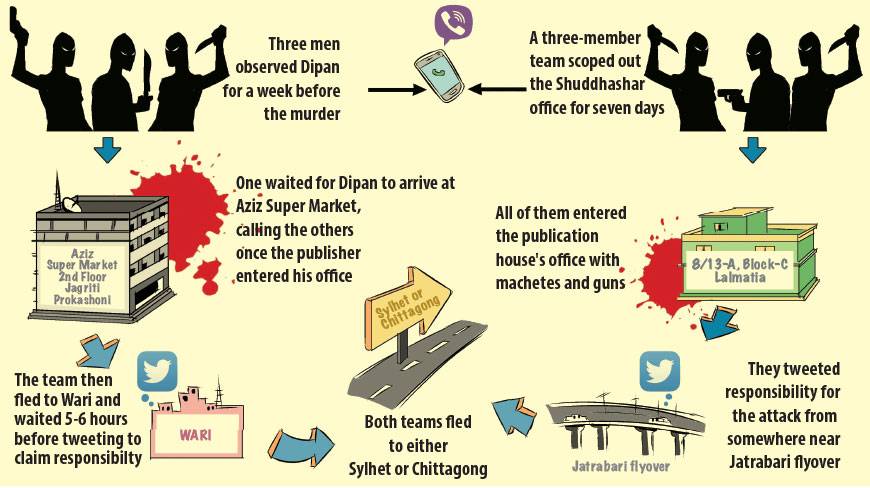
Ahmedur Rashid Tutul, owner of publication house Shuddhashar, and his friends, blogger Ranadipam Basu and poet Tareq Rahim were hacked by the assailants around 2:30pm on Saturday at Tutul’s Lalmatia office in Dhaka.
The hacked dead body of Faisal Arefin Dipan, owner of another publication
house Jagriti, was discovered in his office room in the Aziz Super Market in Shahbagh around 6pm.
Based on autopsy reports that suggested Dipan might have been murdered several hours before that, investigators conclude that the two attacks may well have taken place around the same time.
The IT expert said that militant groups have claimed responsibility within 10 minutes to one hour of such murders and attacks in the past.
So, right after police got the news that Tutul and his friends had been attacked, teams of IT experts started monitoring the 14 internet gateways in the country. Each and every internet activity – starting from Facebook status updates to tweets to emails – must pass through these gateways. They used keywords such as “claim” and “responsibility” for filtering the internet activity passing through the gateways.
Interestingly, the first responsibility claim did not come before 8pm on Saturday, around six hours after the attack on Tutul. The Twitter account of AnsarAlIslam4 posted an update: “Claim regarding assaults on Ahmedur Rashid Tutul & Faisal Arefin Dipon (English).” The tweet was accompanied by the image of an elaborate leaflet that explained why Tutul and Dipan were attacked.
Around 15 minutes later another tweet came with the same words, but this time accompanied by a Bangla version of the same leaflet.
The IT expert said that they at first tracked the internet protocol (IP) address of the ICT-enabled device from which the tweet was made. He could not say for certain which device it has originated from, but it was powered by Android Kitkat 4.4 operating system.
Android Kitkat 4.4 operating systems are found on smartphones and tablets.
Asked what took the militants unusually long to claim responsibility, the expert said: “The killers used proxy servers and VPN to misguide us so that we think that the tweets were made from Syria. In the first layer of tracking, an IP address based in Syria came up. That took them about six hours.
“However, it was only after secondary analysis of the available data that we understood that the tweets were actually made from Bangladesh using proxy servers and VPN,” he said.
VPN (virtual private network) technology is used by individual Internet users to connect to proxy servers for the purpose of protecting personal identity and location.
The investigators initially narrowed down four IP address of the corresponding devices from where the claims were made. Then they tracked these IP addresses back in time and found that these devices were active near the two crime scenes – Lalmatia and Shahbagh – during the time of the attacks.
Investigators have also found activities using the instant messaging application Viber from these devices and thus conclude that the killers might have communicated with each other using this software as well.
At least one of the six members of the killing mission used Viber from inside the Aziz Super Market where Dipan’s office is located.
“These devices were last found on-net in the capital’s Jatrabari and Wari areas on Saturday evening. Then they went off-grid from the digital map. We do not know whether they are still in Dhaka or not.
They might have left the city for Chittagong or Sylhet after committing the murders,” the expert said.
Analysing the movement of the IP addresses, investigators also suspect that the killers have come from outside Dhaka, probably a week ago. All this time they were probably keeping eye on the movement of their targets.
When contacted, Tanvir Hassan Zoha, director of Insight Bangladesh Foundation and focus person of the ICT Ministry’s cyber security programme, said: “We have found that the killers were present in both Aziz Super Market and Lalmatia; but they did not stay there for long. They left just four to five minutes after the incidents.”
He also said that the use of technology was similar in case of both the attacks on bloggers and the Shia procession – only the software used was different.
“Expert killers are now making use of technology along with firearms and sharp weapons. Law enforcers need to be trained up with the technical know-how so that they can tackle such situations,” Tanvir said.
When contacted, Monirul Islam, joint commissioner of police’s detective branch (DB), said that they had yet to find any clue from the closed circuit television camera (CCTV) footage collected from the Aziz Super Market.
“But we are hopeful and are giving maximum importance to technical support to solve the case,” he said.
Yesterday, the charge of investigation of the two cases filed in connection with the attacks was transferred to DB from local police stations.
Source: Dhaka Tribune